Kerala Plus One Computer Application Model Question Paper 1 with Answers
| Board | SCERT |
| Class | Plus One |
| Subject | Computer Application |
| Category | Plus One Previous Year Question Papers |
Time Allowed: 2 hours
Cool off time: 15 Minutes
Maximum Marks: 60
General Instructions to Candidates:
- There is a ‘cool off time’ of 15 minutes in addition to the writing time of 2 hours.
- Use the ‘cool off time’ to get familiar with the questions and to plan your answers.
- Read questions carefully before you answering.
- Read the instructions carefully.
- Calculations, figures, and graphs should be shown in the answer sheet itself.
- Malayalam version of the questions is also provided.
- Give equations wherever necessary.
- Electronic devices except non-programmable calculators are not allowed in the Examination Hall.
Part – A
Answer all questions from 1 to 5. Each carries 1 score. (5 × 1 = 5)
Question 1.
The least Significant Digit (LSD) of (1234.56)10 is
Answer:
6
Question 2.
The process of detecting and correcting errors in a program is called …………
Answer:
Debugging
Question 3.
Name any two keywords in C++.
Answer:
int, float
Question 4.
The memory size required for void data type is ………..
Answer:
0
Question 5.
Rewrite the expression a = a + 1 using an arithmetic assignment operator.
Answer:
a+=1 or a++ or ++a.
Part – B
Answer 9 questions from 6 to 16. Each carries 2 scores each. (9 × 2 = 18)
Question 6.
Find the octal and hexadecimal equivalent of (111101)2.
Answer:
(75)8
(3D)16
Question 7.
Write short note on any two utility softwares.
Answer:
Utilities: Utilities are programs which are designed to assist computer for its smooth functioning. The utilities are given below:
- Text editor: It is used for creating and editing text files.
- Backup utility: Creating a copy of files in another location to protect them against loss, if your hard disk fails or you accidentally overwrite or delete data.
- Compression Utility: It is used to reduce the size of a file by using a program and can be restored to its original form when needed.
- Disk Defragmenter: It is used to speeds up disk access by rearranging the files-that ar& stored in different locations as fragments to contiguous memory and free space is consolidated in one contiguous block.
- Virus Scanner: It is a program called antivirus software scans the disk for viruses and removes them if any virus is found.
Question 8.
Redraw the following flow chart by correcting mistakes.
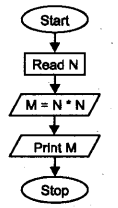
Answer:
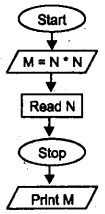
Question 9.
Classify the following into valid and invalid literals and give reason for invalid literals.
33,000+410. 5.6E82
Answer:
33,000 – Invalid since comma cannot be allowed.
+410 – Invalid since real part missing.
5.6E – Invalid since exponent part missing.
82 – Valid
Question 10.
Consider a = 5 and b = 2 and find the result of the following expressions.
a) a>b
b) a! = b&&b>a
Answer:
a) a> b = 5 > 2
It returns true
b) a!=b && b>a
5!=2 && 2>5
true && false
so It returns false.
Question 11.
Write short note on any two statements in C++.
Answer:
Statements: Statements are smallest executable unit of a programming language. Each and every statement must be end with semicolon(;).
1. Declaration statement: Each and every variable must be declared before using it.
Eg: int age;
2. Assignment,statements: Assignment operator is used to assign the value of RHS to LHS.
Eg: X=100;
3. Input statements: lnput(>>) operator is used to perform input operation.
Eg. cin>>n;
4. Output statements: output(<<) operator is used to perform output operation.
Eg: cout<<n;
Question 12.
Briefly explain type promotion with suitable example.
Answer:
Implicit type conversion-: This is performed by C++ compiler internally. C++ converts all the lower sized data type to the highest sized operand. It is known as type promotion. Data types are arranged lower size to higher size is as follows.
unsigned int(2 bytes), int(4 bytes),long (4 bytes), unsigned long (4 bytes), float(4 bytes), double(8 bytes), long double(10 bytes)
Question 13.
Write the equivalent switch statement for the following.
If (ch= = ‘P’)
cout<<“Pass’”
else If (ch= =‘F’)
cout<<“Failed”;
Answer:
switch(ch)
{
case ‘P’:cout<<“Pass”;
break;
case ‘F’: cout<<“Failed”;
}
Question 14.
Define the terms given below.
a) Bandwidth
b) Noise
Answer:
a) Bandwidth: The maximum amount of data that can be transmitted by the medium measured in Hertz.
b) Noise: It is the unwanted electrical or electro-magnetic interferences that adversely affect the transmitted data signals.
Question 15.
Name any four basic elements for data communication:
Answer:
Communication is the exchange of information between two human beings. But data communication is the exchange of, information between two computers (devices).
- Message: It is the data/information to be transmitted from one computer to another.
- Sender: It is a computer or a device that sends data. It is also called source or transmitter.
- Receiver: It is a computer or a device that receives data.
- Medium: It is the path through which message transmitted from the sender to the receiver. There are two types Guided and Unguided media.
- Protocol: The rules and conventions for transmitting data.
Question 16.
Write two advantages of Electronic Payment System (EPS).
Answer:
Electronic Payment System (EPS): It is also called plastic money that is electronically exchange money between two individuals or firms (buyers and sellers) in an online environment.
Part – C
Answer any 9 questions from 17 to 27. Each carries 3 scores each. (9 × 3 = 27)
Question 17.
If (X)16 = (Y)10 = (Z)8 = (11111111 )2 find the values of X, Yand Z.
Answer:
1) To find the value X, i.e. hexadecimal equivalent, divide the binary number into groups of 4 bits and write down the corresponding hexadecimal equivalent.
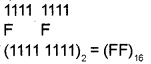
2) To find the value Y, i.e. decimal equivalent, multiply each digit by its corresponding weightage and simply sum it up.
1*27+1*26+1*25+1*24+1*23+1*22+1*21+1*20
=128 + 64 + 32 + 16 + 8 + 4 + 2 + 1
= 255
Here Y = 255
3) To find the value Z, i.e. octal equivalent, divide the binary number into groups of 3 bits and write down the corresponding octal equivalent.
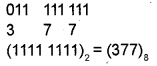
Question 18.
What is e-waste? Explain any two e-waste disposal methods.
Answer:
e-waste(electronic waste): It refers to the mal functioning electronic products such as faulty computers, mobile phones, tv sets, toys, CFL etc.
e-waste disposal methods:
- Reuse: Reusability has an important role of e-waste management and can reduce the volume of e-waste
- Incineration: It is the process of burning e-waste at high temperature in a chimney
- Recycling of e-waste: It is the process of making new products from this e-waste.
- Landfilling: It is used to level pits and cover by thick layer of soil.
Question 19.
Write an algorithm to find the numbers from 1 to 10.
Answer:
Step 1 : Start
Step 2 : Set i=1.
Step 3 : if i>10 go to Step 6
Step 4 : Print i.
Step 5 : Set i=i+1 go to Step 3.
Step 6 : Stop.
Question 20.
Explain any two types of programming errors.
Answer:
In general there are two types of errors syntax errors and logical errors. When the rules or syntax of the language are not followed then syntax errors occurred and it is displayed after compilation. When the logic of a program is wrong then logical errors occurred and it is not displayed after compilation but it is displayed in the execution and testing phase.
Question 21.
Consider the following diagram answer the question.
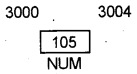
Write the base address (L-value), content (R-value) and Name of variable.
Answer:
Base address (L-value) – 3000
Content (R-value) – 105
Name of variable – NUM
Question 22.
Write short notes on:
a) Preprocessor directive
b) Header file
c) Main () function
Answer:
a) Preprocessor directives: A C++ program starts with the preprocessor directive i.e., # include, #define, #undef, etc, are such a preprocessor directives. By using #include we can link the header files that are needed to use the functions. By using #define we can define some constants. Eg. #define x 100.
b) header files: A header file is a prestored file that helps to use some operators and functions. To write C++ programs the header files are must.
Following are the header files
- iostream
- cstdio
- cctype
- cmath
c) The main function: The main function is the first function which is invoked at the time of execution and the program ends within main(). The other functions are invoke from main().
Question 23.
What is the use of type modifiers in C++? List any four type modifiers.
Answer:
Type modifiers: With the help of type modifiers we can change the sign and range of data with same size. The important modifiers are signed, unsigned, long and short.
Question 24.
Write a C++ program to input an integer and check whether it is positive, negative or zero.
Answer:
#include<iostream>
using namespace std;
int main()
{
int n;
cout<<“Enter a number”;
cin>>n;
if(n>0)
cout<<“The number is positive”;
else if(n<0)
cout<<n<<“The number is negative”;
else
cout<<n<<“The number is zero”;
}
Question 25.
Compare Dial-up connection and wired broadband connection.
Answer:
| Dial-up Connection | Broadband connection |
| 1. Requires dialing to ISP | 1. Always on connection |
| 2. Slow speed | 2. High speed |
| 3. Error rate is low | 3. Error rate is high |
| 4. Uses dial-up modem | 4. Uses broadband modem |
| 5. Exclusive telephone line needed | 5. Simultaneously transmit voice and data |
Question 26.
a) Consider the following e-mail address and write the user name and domain name of it. [email protected]
b) List any four advantages of e-mail.
Answer:
a) Username – myschool
Domain name – gmail.com
b) The advantages of e-mail are given below:
- Speed is high
- It is cheap
- We can send email to multiple recipients
- Incoming messages can be saved locally
- It reduces the usage of paper
- We can access mailbox anytime and from anywhere.
Question 27.
Explain any three IT-enabled services.
Answer:
1. e-Governance: The integration of computers and communication technology for the benefit of government functions to the public is termed as e-Govemance by this government can serve the public in a convenient, efficient and transparent manner.
2. e-business(electronic Business): Providing services or running business through internet is called e-business.
3. e-Learning: It is the use of electronic media (It includes text, audio, video, image, animation, etc), educational technology. (It includes Satellite TV, CD ROM, Computer Based Learning, etc) and information and communication technologies (ICT – it uses intranet/extranet and web-based learning) in education.
Part – D
Answer any 2 questions from 28 to 30. Each carries 5 scores each. (2 × 5 = 10)
Question 28.
“Open source softwares are getting more popularity all over the world today.”
a) Write the full form of FSF.
b) Briefly elaborate four freedoms of open source softwares.
c) Give four examples of open source softwares.
Answer:
a) Free Software Foundation
b) The Four freedoms are
i) Freedom 0 : To run program for any purpose
ii) Freedom 1 : To study how it works and allows you to adapt according to your needs. Also allows to access source code.
iii) Freedom 2 : Allows to take copies and distribute
iv) Freedom 3 : Allows you to change source code and release the program.
c) Examples for Free and open source software are given below:
- Linux
- GNU/Linux: It was organized by Richard Stallman in 1983
- GIMP (GNU Image Manipulation Program)
- Mozilla Firefox
- OpenOffice.org
Question 29.
a) List the four different parts of a loop in C++.
b) Compare while loop and do-while loop with suitable example.
Answer:
a) Different parts of a loop
- Initialization: The loop variable must be initialized. Eg: i=0;
- Checking: The variable must be checked before each iteration. Eg: i<=10;
- Updation: The loop variable must be updated. Eg: i++;
- Body: Body of the loop to be executed. More than one statement then enclosed in curly braces({,}).
b)
| while loop | do-while loop |
| 1. Entry controlled | 1. Exit controlled |
| 2. If the condition is false in the beginning the body will not execute | 2. Even though the condition is false in the beginning, the body of the loop will be executed once |
Question 30.
a) Define topology. (1)
b) Explain any two topology. (2)
c) Differentiate HUB and SWITCH. (2)
Answer:
a) Network topologies: Physical or logical arrangement of computers on a network is called structure or topology. It is the geometrical arrangement of computers in a network. The major topologies developed are star, bus, ring, tree and mesh.
b) 1) Star Topology : A star topology has a server all other computers are connected to it. If computer A wants to transmit a message to computer B. Then computer A first transmit the message to the server then the server retransmits the message to the computer B. That means all the messages are transmitted through the server. Advantages are add or remove workstations to a star network is easy and the failure of a workstation will not effect the other. The disadvantage is that if the server fails the entire network will fail.
2) Bus Topology: Here all the computers are attached to a single cable called bus. Here one computer transmits all other computers listen. Therefore it is called broadcast bus. The transmission from any station will travel in both the direction. The connected computers can hear the message and check whether it is for them or not.
Advantages are add or remove computer is very easy. It requires less cable length and the installation cost is less, disadvantage is fault detection is very difficult because of no central computer.
c) Hub: It is a small, simple and inexpensive device used to connect computers (devices) to a network. If a computer wants to transmit data to another computer. First it sends to the hub, the hub retransmits this data to all other computers. Each and every computer gets the data and check whether it is for them or not. It increases the network traffic and hence the transmission speed is low.
Switch: It is an expensive device used to connect computers(devices) to a network. Unlike hub, switch transmit data not to all computers, it retransmits data only to the intended computer. So the traffic is less and speed is high
We can summarise it as follows
| Hub | Switch |
| 1. It is cheap | 1. It is expensive |
| 2. It is not an intelligent device | 2. It is an intelligent device |
| 3. High traffic | 3. Less traffic |
| 4. Low speed | 4. High speed |